Let’s face it, as technology becomes increasingly integrated into our daily lives, cybersecurity is more important than ever. You rely on your devices and internet connectivity for everything from work to personal relationships, so protecting your digital life should be a top priority. One of the best ways to boost your cybersecurity is by implementing device posture checks with your VPN. Never heard of them? No worries, we’ve got you covered. Device posture checks allow you to ensure your devices meet certain security standards before connecting to a network. By integrating them with your VPN, you can rest assured your data and privacy are protected every time you go online. Read on to discover three simple ways you can take your cybersecurity to the next level with device posture checks and VPN integration. The future of technology is exciting, but it’s up to you to make sure it’s secure!
1. Require Device Posture Checks When Connecting to the VPN
Want to boost your network security in an upbeat way? Requiring device posture checks when connecting to your VPN is an energizing first step!
- Make device posture checks mandatory for all systems accessing your VPN. This cheerful policy ensures that only trusted and properly secured devices can connect to your network resources.
- Define your device security criteria in an inclusive way. You’ll want to check that systems have a firewall enabled, current OS and software updates installed, and an antivirus program running. Be flexible though – some devices may require alternative security controls.
- Choose an automated device posture check solution. Manual checks are tedious and time-consuming. Automated solutions are efficient, accurate and allow your IT team to focus on more engaging tasks!
Implementing mandatory device posture checks when accessing your VPN will give you an uplifting sense of improved security. No more worrying about vulnerable systems compromising your network! Your users will also appreciate a policy that protects their information in a constructive way.
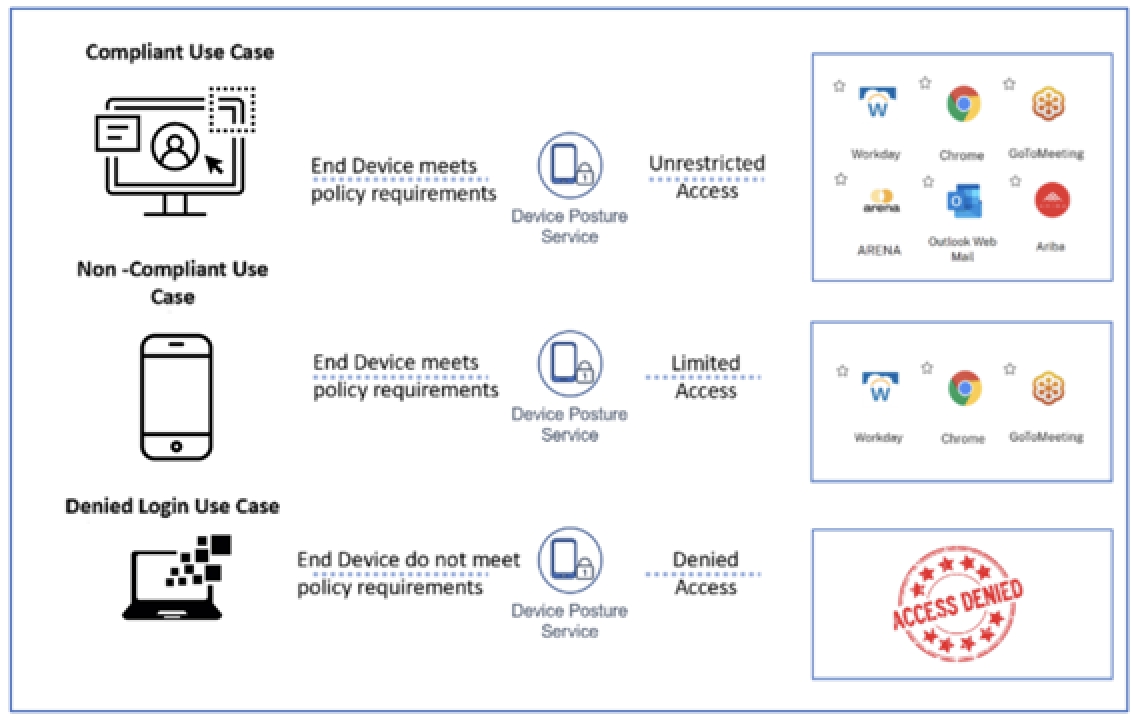
Overall, device posture checks are an energizing step toward robust network security. They are efficient, improve visibility into the security status of systems accessing your VPN and help close backdoors into your network. Approach them with enthusiasm and optimism for better protection of your resources and an improved security posture! Using an automated device posture check solution makes the process downright cheerful. What are you waiting for? Dive in and boost your network security today!
2. Set Device Posture Policies and Enforce Them
You’ll want to set clear device posture policies to ensure your VPN and network stay secure. The good news is, it’s easy to do and will give you peace of mind!
- US Data Protection: Online Habits and Data Breaches Define what a healthy device looks like. Things like an up-to-date OS, current antivirus software, and a secure password policy are must-haves. You’ll also want to mandate things like disk encryption and firewalls.
- Set policies in your VPN app. Most business VPN solutions let you establish device posture checks right in the admin console. Select the requirements you want to enforce, like requiring a passcode on mobile devices or disabling USB drives. Then apply the policy to user groups.
- Check device health automatically. The best VPNs will scan devices whenever a user logs in to ensure they meet your standards. If not, the user will be prompted to take action before accessing the network. This helps guarantee every device accessing your VPN is in tip-top shape.
- Get reports on non-compliant devices. Stay on top of any devices that don’t meet your policies through detailed reports. Then you can take appropriate action, whether that’s remediating issues or restricting network access.
Keeping devices secure has never been so simple! By setting clear policies, enforcing them automatically, and monitoring compliance, you can rest easy knowing your users have healthy, posture-checked devices accessing your network. VPNs make device security a breeze so you have time to focus on more important things – like growing your business!
3. Get Notified When Devices Fail Posture Checks
Get Notified Immediately
You’ll want to know right away if any of your devices fail a posture check, so set up notifications. Most VPN solutions offer options to alert you through email, text, or right in the admin console. Turn them all on! The sooner you’re aware of an issue, the quicker you can take action to remediate it.
Staying on top of device posture is key to keeping your network secure. Don’t leave it to chance – enable notifications to get the news as soon as possible. You’ll feel so much more at ease knowing you have this important info delivered directly to you. Think of it as an extra layer of protection and peace of mind!
Once notified, log into your VPN console to see details on the failed check. Look for things like missing software patches, insecure configurations, or other vulnerabilities. Then you can promptly fix the problem and rerun posture checks to confirm remediation. Nice work – your network will be locked up tight again in no time!
Regular Reporting
In addition to real-time alerts, generate regular compliance reports to review device posture across your network. Weekly or monthly reports are ideal. Look for any trends in failures or areas that could use improvement. These routine checkups, combined with prompt notifications on failures, will help ensure you have continuous visibility and control over the security of all connected devices.
Staying vigilant with device posture doesn’t have to be difficult or time-consuming. With the right VPN solution handling automated checks and delivering alerts when needed, you’ll gain peace of mind knowing your devices meet compliance standards to keep threats at bay. Implementing regular reviews of reports provides an extra layer of assurance your network is locked down and any issues are addressed right away. Stay cheerful – your security posture will be strengthened in no time!
4. Automate Device Quarantine After Failed Checks
Automating device quarantine after failed checks is a must to ensure compromised devices don’t gain access to your network. As soon as a device fails its posture check, it should immediately be blocked from connecting to VPN. This helps guarantee that insecure endpoints can’t access sensitive data or resources.
Set Clear Policies
Define explicit policies in your VPN solution outlining the conditions that will trigger a device to be quarantined. For example, if a device is missing a required software update or has an outdated antivirus solution, it fails the check. Be very specific to avoid confusion.
Enforce Quarantine Immediately
As soon as a device fails a check, it should be quarantined without delay. Don’t give non-compliant devices a grace period to connect, or you risk compromising your network security. Enforce quarantine the moment an issue is detected.
Notify Users Promptly
Alert users right away that their device has been blocked from VPN access and provide clear details on the reason for quarantine. Let them know exact steps to take to remediate the issue so they can get reconnected as quickly as possible. The faster they can resolve the problem, the less impact there is to productivity.
Require Remediation to Reconnect
Don’t just lift quarantine without ensuring the underlying issue has been fixed first. Require users to confirm they have updated software, enabled antivirus, or taken other necessary actions before removing the device from your blocked list. Only then should they be granted access to VPN again.
Staying on top of device health and hygiene is crucial to network security. Automating device quarantine helps ensure non-compliant systems don’t jeopardize your infrastructure while also keeping users informed and productive. With clear policies, immediate enforcement, prompt notifications, and required remediation in place, you can integrate device posture checks with confidence!
Related Article : How to Watch beIN Sports Online From Anywhere Using VPNs
Consider a Standalone Device Posture Solution
A Standalone Solution is a One-Stop Shop
If you want an all-in-one solution to manage your device security posture, consider deploying a standalone device posture product. These specialized tools are purpose-built to automate device compliance checks and remediation. They can save your team time and effort in keeping endpoints protected.
A standalone option typically provides a centralized console to set policies, run reports and gain visibility across your entire fleet from a single pane of glass. No need to configure multiple systems or worry about integrating different vendor solutions. How easy is that?!
Set It and Forget It
The best part about a standalone device posture product is that they are designed to do the heavy lifting for you. Simply define your device compliance policies, like requiring a firewall, disk encryption and the latest OS patches, and the solution will automatically check endpoints for violations. If any devices are found out of compliance, the product can fix many issues on its own without admin intervention. Talk about convenience!
More Robust Capabilities
Dedicated device posture solutions often have more robust features than what you may find built into other tools like a VPN. Things like:
- Automated remediation to resolve policy violations
- Advanced reporting and dashboards to monitor compliance
- Support for a wider range of device types like servers, routers and IoT devices in addition to laptops and desktops
- Tamper protection to prevent users from disabling security controls
- Integration with other systems like your SIEM, patch management and AV consoles for a centralized view of device health
Using a standalone device posture product is a simple way to strengthen your overall security stack. When endpoints are properly secured and managed, you can rest easy knowing your sensitive data and systems are well protected. Sweet dreams!
Conclusion
So there you have it, three ways to integrate device posture checks with your VPN for enhanced security and compliance. By implementing even one of these techniques, you’ll take your network security to the next level and have confidence that only trusted and properly secured devices are accessing sensitive resources. What are you waiting for? Talk to your network and security teams today about rolling out device posture checks. Your organization’s data and infrastructure will thank you, and you’ll sleep better at night knowing you’ve reduced risk across the board. The future is here – are you ready to embrace it? With the right strategy and tools in place, you’ll be well on your way to a new world of network access and authentication. The possibilities for stronger security and streamlined management are endless if you make device posture checks a priority. So get to it and good luck securing your network! The rewards of enhanced security and compliance are well worth the effort.